Cyber attack recovery plan template (step by step)

Are cyberattacks really a rare exception anymore?
Recent surveys show that cyberattacks are now a routine part of doing business rather than rare exceptions. A Cloudflare study of more than 4,000 business and technology leaders across 13 European markets found that 72% of organisations had experienced at least one cybersecurity incident in the previous 24 months, and 40% had been hit in just the last year.
Yet many companies still rely on recovery plans that look convincing on paper but fall apart the moment ransomware hits. Backups fail, procedures are unclear, and compliance obligations are forgotten in the chaos. In this article, you’ll find a practical recovery plan template designed to be both GDPR-compliant and resilient against modern ransomware attacks.

Why every business needs a cyber attack recovery plan
A cyberattack can shut down critical systems and cause downtime that can result in thousands or even tens of thousands of euros in losses per hour. For many companies, the operational disruption caused by downtime exceeds the damage done by the attack itself.
On top of the financial impact, every organisation operating under GDPR faces strict reporting requirements. If personal data is compromised, the business must notify authorities within 72 hours and may face fines of up to €20 million or 4% of global turnover.
A dependable recovery plan is essential for business continuity.There is a growing tension between international legislation such as the U.S. CLOUD Act and European data protection laws, where companies relying on non-sovereign cloud services may unintentionally expose themselves to legal conflicts. A GDPR-aligned recovery plan must therefore ensure that critical recovery data resides in a privacy-safe, sovereign infrastructure (and not just on a marketing sheet, but truly sovereign)
What’s a typical mistake in recovery planning?
“A backup that hasn’t been tested isn’t really a backup, it’s a copy,” as our COO once famously said. This becomes painfully true during a ransomware incident. Attackers often go after backups first, corrupting metadata, deleting recovery points, or encrypting snapshot repositories before you even realise an intrusion has happened.
Traditional backup systems frequently fail under real pressure because they rely on always-on access, shared credentials, and replication mechanisms that may copy the infection into the backup. When recovery data is compromised, companies are left without a clean restore point and are often forced into paying the ransom simply to resume operations. Once that payment channel is open, you can start calculating ransom payments into your yearly budget.

GDPR and ransomware requirements for recovery plans
A GDPR-compliant recovery plan must support the ability to restore personal data quickly and reliably. Article 32 specifically requires organisations to maintain the availability and resilience of systems, which means demonstrating that recovery procedures actually work.
If personal data is affected, the organisation must make internal notifications immediately and submit a formal report to authorities within 72 hours. If the risk to individuals is considered high, affected people may need to be contacted as well.
Ransomware incidents create both technical and legal risks. The organisation must not only stop the attack and restore operations but also document the incident, prove the integrity of recovered data, and show regulators that the recovery process follows GDPR principles.
Immutable backups are your last line of defence
Immutable backups provide the strongest protection by creating recovery data that cannot be altered or deleted, even by administrators. These backups are time-locked and isolated from production systems, making them resistant to tampering, encryption, or corruption.
Their importance becomes clear when ransomware happens. Because attackers cannot modify or destroy these backups, organisations always retain a clean, unaffected recovery point. Immutable backups have become the foundation of any ransomware-ready recovery strategy, and they offer a dependable safety net that traditional backup systems simply cannot match.
Why immutability matters
- Block attackers from wiping recovery points
- Prevent ransomware from encrypting or modifying historical data
- Guarantee that a clean copy of your systems always exists
Cyber attack recovery plan template (step by step)
Use this as your internal recovery blueprint.
1. Identify critical systems and data and prioritise them based on business impact
List essential systems, such as:
- Authentication (IdP, AD)
- Email and communication tools
- Finance and ERP
- Customer data platforms
- Operational systems
2. Define roles and responsibilities, because clear ownership prevents chaos
Specify who does what during a cyber incident:
- IT / Security: containment, forensics, recovery
- Management: decisions, budgeting, external communication
- Legal / DPO: GDPR reporting, regulator communication
- PR / Communications: external messaging
3. Establish communication procedures and ever rely on production systems that may be offline during an attack
Document the following:
- Internal alerting and escalation
- Communication with the DPA
- Communication with customers and stakeholders
- Approved channels (e.g., non-compromised communication tools)
4. Backup and recovery strategy
A GDPR-ready and ransomware-ready strategy must include:
- Immutable backups stored in GDPR-compliant, sovereign infrastructure
- Offline or isolated backup copies
- Regular integrity checks
- Documented restoration procedures
- Multiple recovery points to avoid reinfection
5. Backup is not a backup without regular testing
Schedule regular:
- Disaster recovery drills
- Ransomware simulation exercises
- Recovery time validation
- Backup restoration tests
6. Continuous monitoring and updating
Update the plan annually or when:
- Infrastructure changes
- New systems are added
- Regulations evolve
- You complete a major incident review

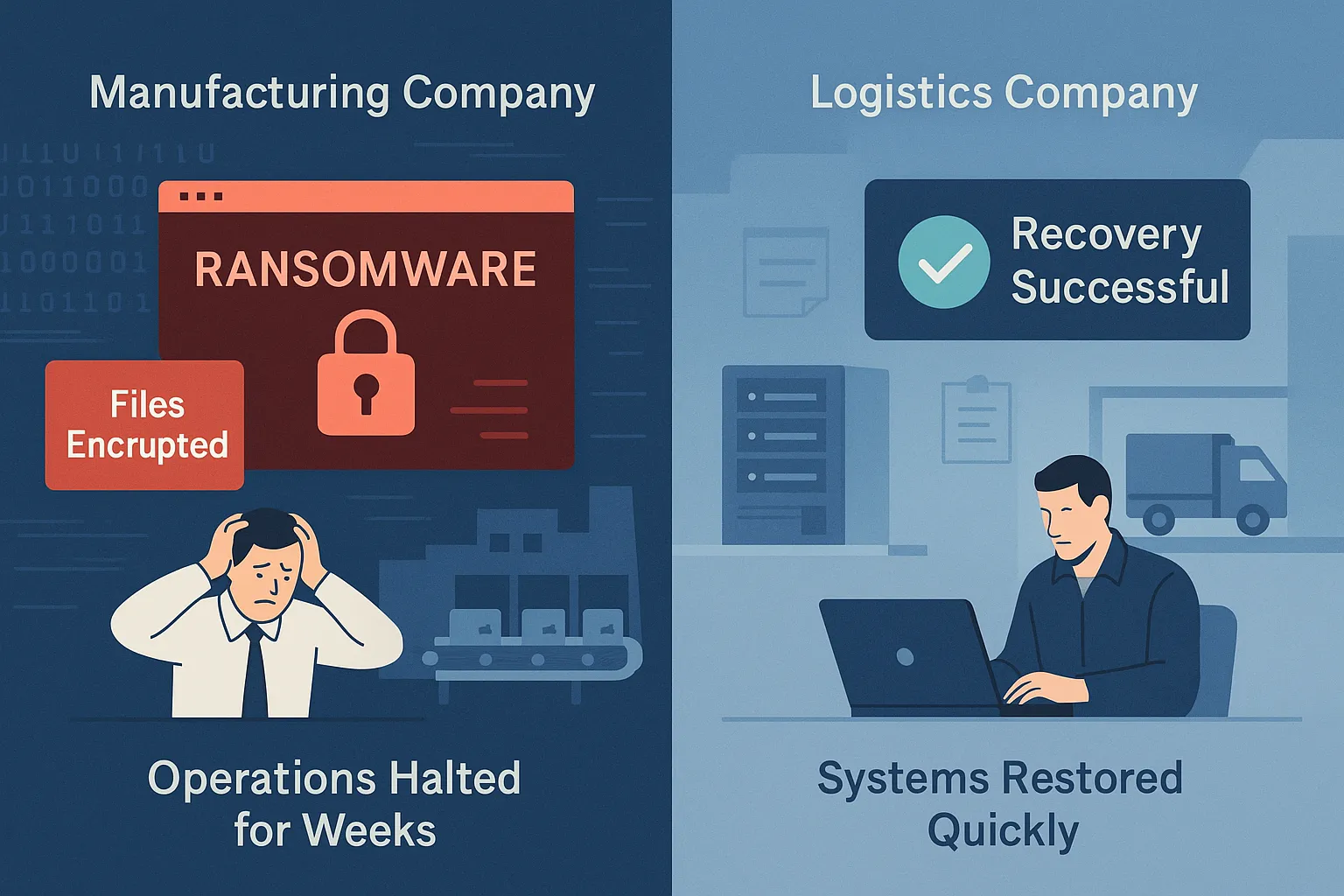
Case example: Recovery with vs. without immutable backups
Consider the case of a manufacturing company whose backup repository was encrypted during an attack. Without clean recovery data, its ERP system was offline for nearly two weeks, resulting in more than a million euros in losses, a mandatory breach notification and a lengthy cleanup process. The company ultimately paid the ransom but still faced severe operational consequences.
In contrast, a logistics company using immutable backups recovered from a similar attack within the same day. Their clean recovery point was untouched, enabling them to restore critical systems in hours without paying the attackers or risking customer data exposure.
The difference between these two outcomes highlights that the presence or absence of immutable, tested backups often determines whether a company can keep smooth sailing and business continuing, or make a big payday possible for cybercriminals.
Cyberattacks are now a certainty. Recovery is the part you control. Preparing today ensures that your organisation can hold the fortress up during and after a cyberattack




